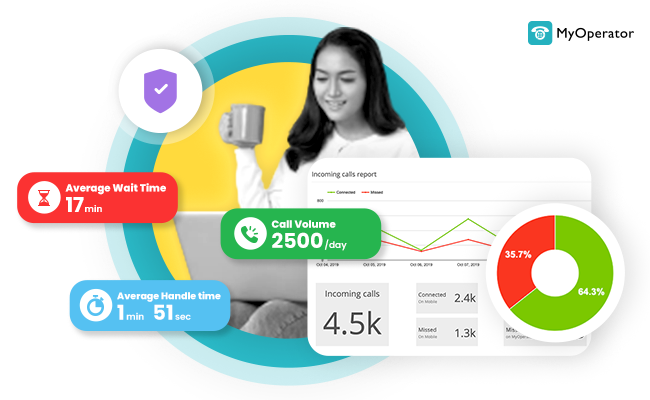
Providing the highest level of protection to customer data stands as the ultimate testament of loyalty and gratitude that businesses can extend to their clientele. Nowadays, call center data protection has become a paramount concern for businesses operating call centers, particularly in India: a global hub for call center operations.
As companies leverage call centers to engage with customers, provide support, and drive sales, they simultaneously grapple with the responsibility of safeguarding sensitive customer information.
This responsibility extends not only to ethical considerations but also to legal obligations imposed by the country’s data protection regulations.
Speaking of, Indian call center software providers employ active measures such as encryption for data at rest and in transit, firewalls and intrusion detection systems to prevent unauthorized access.
To ensure compliance with global call center data protection regulations these providers implement strict controls and adhere to international standards.
This article explores the critical nexus between security, SOX compliance, and call center data and customer data protection within the context of call center operations in India.
Let’s mull over the in-depth details of data security and compliance in India.
Why is Security and Compliance in Call Center Software a Must? Explained in Detail
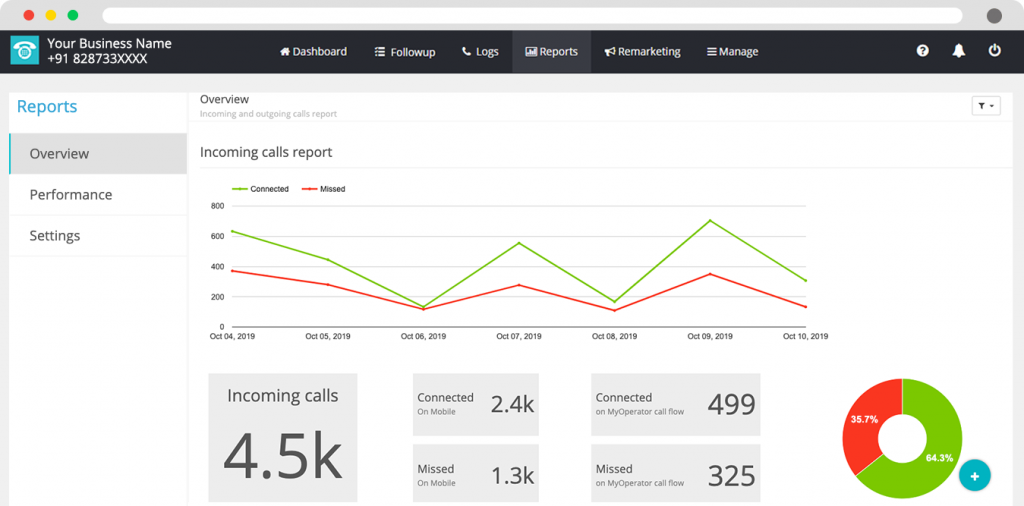
Security and compliance in call center software providers are imperative for several reasons, Let’s delve into the individual importance of security and compliance in call centers.
Protection of Sensitive Customer Data
- Confidential Information Handling: Call centers routinely handle a wide range of sensitive customer data, including personal identification information (PII), financial data, healthcare information, and more. This information is entrusted to businesses by their customers, and it is the duty of the call center to safeguard it from unauthorized access or breaches.
- Trust and Reputation: Customers expect their data to be handled with care and confidentiality. A data breach can result in the loss of trust, reputation damage, and a loss of customers, which can have severe financial implications.
Legal and Regulatory Obligations
- Global Data Protection Laws: Many countries have implemented strict data protection laws such as the General Data Protection Regulation (GDPR) in the European Union, the Health Insurance Portability and Accountability Act (HIPAA) in the United States, and the California Consumer Privacy Act (CCPA).
- India’s Information Technology Act, 2000: This foundational law governs electronic transactions and provides a legal framework for data protection and cybersecurity in India.
MyOperator is proud to be ISO/IEC 27001:2013 compliant, a testament to its commitment to data security.
Compliance with this act is pivotal for ensuring the security of customer data.These laws require businesses to handle customer data with the utmost care, or they risk severe fines and legal penalties for non-compliance.
- Data Breach Notification: Regulations often require organizations to promptly notify affected individuals and authorities in case of a data breach. Failing to do so can result in additional penalties.
- Liability: Non-compliance with data protection laws can lead to legal liability and lawsuits from affected customers, potentially resulting in significant financial losses.
Financial Implications
- Fines and Penalties: Regulatory bodies have the authority to impose substantial fines for data breaches and non-compliance. These fines can run into millions of dollars, depending on the severity of the breach and the jurisdiction.
- Loss of Revenue: Data breaches and security incidents can lead to customer churn and revenue loss. Customers may take their business elsewhere if they do not trust a company to protect their data.
Operational Continuity
- Disruption Mitigation: A data breach or security incident can disrupt call center operations, causing downtime and impacting customer service. Investing in security measures and compliance helps mitigate such disruptions.
- Reputation Damage: Security incidents can lead to negative media coverage and damage a company’s reputation. Rebuilding trust can be a lengthy and costly process.
Competitive Advantage
- Market Differentiation: Companies that prioritize security and compliance can use this as a competitive advantage. They can advertise their commitment to data protection, potentially attracting more privacy-conscious customers.
- Business Opportunities: Compliant call centers are better positioned to handle contracts from industries with stringent regulatory requirements, such as healthcare or finance.
Data Breach Cleanup Costs
- Remediation Costs: In the aftermath of a data breach, businesses must invest in remediation efforts, including forensic investigations, system repairs, and customer notification. These costs can be substantial.
- Rebuilding Trust: Rebuilding trust with customers after a breach may involve offering identity theft protection services or other forms of compensation, adding further financial strain.
Best Practices for Safeguarding Customer Data
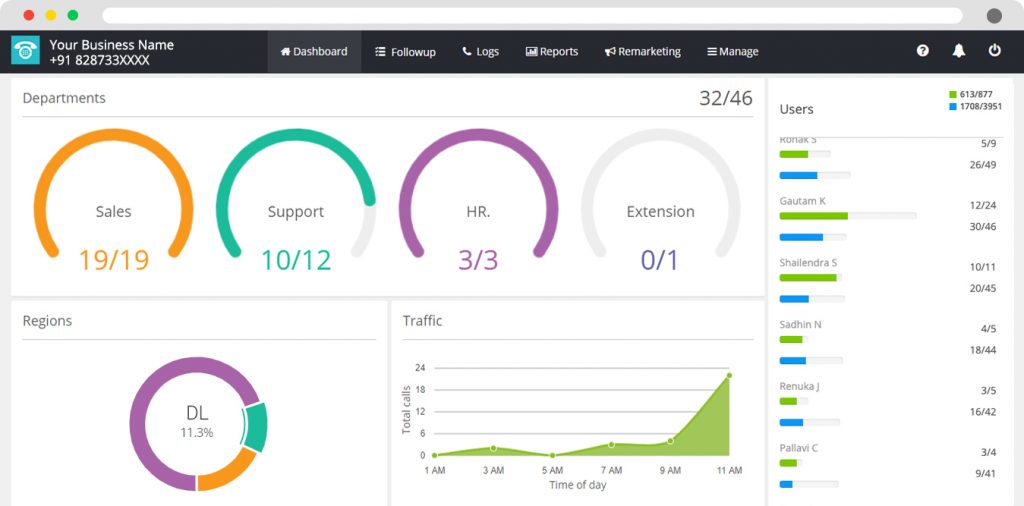
Call center software providers, like MyOperator, implement several best practices to protect customer data.
These practices not only ensure data security but also facilitate compliance with data protection regulations.
Here are some of the best practices employed by remote call center software providers in India for safeguarding customer data
Encryption of Data
Utilizing robust encryption techniques is akin to locking sensitive data in an iron vault.
Imagine you’re sending a confidential email to a colleague. Encryption scrambles the contents of that email into a code that only the recipient can decipher/read.
Even if someone intercepts the email, they’ll be left with a jumble of characters, rendering the information useless.
Similarly, when data is “at rest” – stored on servers or devices – encryption ensures that even if an illegal; party gains access, they’ll find nothing but gibberish.
MyOperator’s business IVR solution (Interactive Voice Response) plays a crucial role in the context of data encryption.
Just like encryption secures digital communication, IVR provides a secure and efficient way for customers to interact with businesses over the phone.
When a customer calls, IVR system prompts them to enter information like their account number or PIN, which is then encrypted and processed securely.
This encryption ensures that sensitive customer data remains confidential during the interaction, making it as secure as the process of sending a confidential email with encryption.
MyOperator’s IVR solution not only enhances security but also streamlines customer interactions, creating a win-win scenario for businesses and their customers
Access Control and Authentication
Think of access control as a bouncer at an exclusive club. Not everyone gets in; only those with the right credentials do.
Role-Based Access Control (RBAC) works similarly. It grants access to specific areas of data or systems only to authorized individuals based on their roles.
For example, a customer service representative should have access to customer records but not to financial data. Multi-Factor Authentication (MFA), on the other hand, is like having two locks on your front door – you need both a key and a passcode to enter.
It adds an extra layer of security by requiring multiple forms of verification, such as a password and a fingerprint scan, before granting access.
Regular Security Audits
Think of a security audit as a health checkup for your organization’s data. Just as you visit a doctor to catch and treat health issues before they become serious, regular security audits help identify and address vulnerabilities in your systems and processes before they can be exploited by cybercriminals.
It’s like having a security expert examine your digital infrastructure to find weak points and fix them. In addition to internal audits, third-party security audits are like getting a second opinion – they provide an unbiased evaluation of your security measures.
Incident Response Plan
An incident response plan is your emergency protocol for navigating through stormy waters.
It outlines precise steps to take in case of a data breach – a security incident. Think of it as a digital fire drill.
Having a well-defined incident response plan in place ensures that when a breach occurs, your team knows exactly what to do.
Rapid response is crucial in minimizing the impact of a security incident, much like how a well-rehearsed fire drill can save lives in an emergency.
Employee Training
Consider employee training as the foundation of your data security fortress. It’s about educating your team on best practices, compliance requirements, and the importance of data security.
Just as a well-trained army, a workforce educated in data protection is the first line of defense against cyber threats.
Training programs empower employees to recognize and respond to security threats, making them vital guardians of your organization’s data.
Data Masking and Redaction
Call Data masking and redaction are like using blackout curtains on your windows. They protect sensitive information from prying eyes.
Let’s assume a scenario where you’re a call center agent assisting a customer. You need access to their account information, but you don’t need to see their credit card number or social security details.
Data masking and redaction techniques ensure that you only see what’s necessary for your task – like the necessary information on a document with confidential sections blacked out.
Data Retention Policies
Data retention policies are like digital home cleaning before a festival. Just as you wouldn’t keep old newspapers piled up in your home, companies shouldn’t hold onto customer data longer than necessary. These policies define how long customer data should be stored.
For example, if a customer’s contract has expired, retaining their data for an extended period is unnecessary and increases the risk of exposure.
It’s essential to regularly review and delete or anonymize data that is no longer needed to minimize exposure.
Secure Telecommuting Practices
In today’s remote work environment, employees accessing customer data from home need to do so securely.
Using VPNs and secure connections is akin to ensuring that their journey – data transmission – is safe from potential threats along the way.
This way, employees can work remotely while safeguarding sensitive information.
Vendor Due Diligence
Vendor due diligenceis like interviewing a contractor before letting them into your home. When third-party suppliers and vendors handle customer data, it’s crucial to ensure they meet high-security standards.
Just as you’d check references and credentials before hiring someone to work on your house, vetting and performing due diligence on third-party vendors ensure they adhere to robust security measures when handling customer data.
Compliance with Data Protection Laws
Compliance with laws, particularly those related to call center data protection, is like following traffic rules. Just as obeying speed limits and traffic signals keeps you safe on the road, adhering to data protection laws ensures that your organization is legally compliant when handling customer data.
International regulations like GDPR and domestic laws like India’s Information Technology Act set the rules for data handling, protecting both businesses and consumers.
Data Backups and Recovery
Data backups and recovery, crucial for call center data protection, are like having insurance for your data. You hope you’ll never need it, but it’s crucial in case of a disaster.
Regularly backing up customer data is akin to creating copies of valuable documents.
In case of data loss due to unforeseen circumstances, robust disaster recovery plans ensure that your organization can recover and continue operations seamlessly, just as insurance helps you bounce back after an accident.
Secure Data Centers
Secure data centers provide a fortified environment for hosting your call center software, including shared web hosting solutions.
With physical security measures, access controls, and redundancy, these data centers ensure that your data remains impervious to physical threats, much like a high-security bank vault.
Regular Software Updates and Patch Management
If you own a car or bike then regular software updates and patch management is similar to the maintenance you do to maintain your vehicle.
Just as changing the oil and keeping the engine in top condition ensures your car runs smoothly, keeping your call center software and systems up to date with the latest security patches is essential to address vulnerabilities. It’s like ensuring your vehicle’s safety features are functioning optimally.
Audit Trails and Logging
Audit trails and logging are like a digital surveillance system in your organization. They maintain a record of user activities within the system, acting as a watchful eye.
Providers like MyOperator maintain comprehensive audit trails and logs of user activities within the system, acting as a digital surveillance system for your organization.
These logs can be crucial for monitoring and investigating security incidents, offering you peace of mind in knowing that your data is under watchful eyes.
How MyOperator Protects Customer Data as a Call Center Software Provider for Businesses?
Data security is of paramount importance in today’s digital age, where businesses rely heavily on call centers to engage with customers, offer support, and drive growth.
MyOperator, one of India’s leading cloud call center software providers, recognizes the critical role it plays in safeguarding customer data.
MyOperator is proud to be ISO/IEC 27001:2013 compliant, a testament to its commitment to data security.
1. Encryption and Secure Transmission
The absence of encryption and secure transmission in call center software exposes businesses to a range of critical issues.
It increases the risk of data breaches, leading to potential legal consequences, loss of customer trust, and reputation damage.
Financial losses may occur due to breach-related costs, operational disruptions, and regulatory fines for non-compliance, particularly in regulated industries.
This security gap also puts businesses at a competitive disadvantage and makes it challenging to address insider threats effectively.
Overall, encryption and secure transmission are essential safeguards to protect customer data and maintain the integrity and reputation of the business
When you opt for MyOperator as your virtual call center software service provider, you get state-of-the-art encryption protocols to secure customer data both in transit and at rest.
This means that data is unreadable to unauthorized individuals, even if intercepted during transmission.
Secure socket layer (SSL) and transport layer security (TLS) encryption are employed to protect data during communication between the call center software and clients’ systems.
2. Role-Based Access Control (RBAC)
The absence of Role-Based Access Control (RBAC) in call center software can result in significant problems for businesses. It leads to data vulnerability, misuse, and privacy violations, increasing the risk of data breaches and legal consequences.
Operational inefficiencies arise as employees struggle to access relevant data, while compliance issues can result in fines and penalties.
The absence of RBAC also heightens security threats and complicates user management, especially as businesses scale. Moreover, tracking and auditing user activities becomes challenging, hindering the investigation of security incidents.
In essence, RBAC is essential for data security, compliance, operational efficiency, and accountability, particularly in safeguarding customer data which is why MyOperator’s call center software is the best in the market.
As your call center software provider, MyOperator offers RBAC mechanisms that grant access to customer data based on predefined roles and responsibilities.
Only authorized personnel can access sensitive information, reducing the risk of data breaches caused by internal threats.
3. Compliance with Data Protection Laws
MyOperator diligently adheres to data protection regulations, both international and domestic. Let’s just say you opt for a provider that doesn’t comply with data protection laws.
Here’s how it goes. When a call center software provider lacks compliance with data protection laws as a feature for businesses, it gives rise to numerous critical issues.
Chief among them is the risk of legal non-compliance, exposing businesses to hefty fines and legal repercussions for failing to adhere to stringent data protection regulations.
This absence also leaves businesses vulnerable to data breaches, potentially resulting in data exposure and lawsuits.
Furthermore, it erodes customer trust as individuals expect their personal information to be handled in accordance with the law.
Navigating the complex landscape of data protection regulations becomes challenging without compliance features, leading to regulatory challenges and increased data handling complexity.
Inefficient compliance audits, limitations in international business operations, and data security gaps further compound the problems.
By staying current with evolving legal requirements, MyOperator ensures that its call center software service facilitates compliance for businesses.
4. Regular Security Audits
There are several adverse impacts on businesses when call center software providers fail to conduct regular security audits.
Firstly, it increases the risk of security vulnerabilities going unnoticed, leaving the business exposed to potential cyber threats and data breaches.
Without routine audits, businesses may struggle to identify and rectify weaknesses in their systems and processes, potentially leading to operational disruptions and financial losses.
Moreover, the absence of third-party security audits can result in a lack of unbiased evaluation of security measures, making it difficult for businesses to gauge their security posture accurately.
However, if businesses opt for MyOperator cloud-based call center solutions in India, they can overcome these challenges effectively.
MyOperator offers regular security audits as part of its comprehensive security measures. These audits help businesses identify vulnerabilities, weaknesses, and areas for improvement in their call center operations.
With third-party security audits, MyOperator provides an impartial evaluation, ensuring that businesses receive an unbiased assessment of their security measures.
Such an exclusive feature not only helps protect customer data but also strengthens the overall security posture of the business, fostering trust and confidence among customers and stakeholders.
5. Data Retention and Deletion Policies
It is important to understand the data retention and deletion policies of your providers because data can make or break the business. There are many hazards if the provider does not comply with data retention policies.
To begin with, it can lead to data hoarding, where unnecessary customer data is retained for extended periods, increasing the risk of data breaches and unauthorized access.
Many businesses are prone to security risks, and struggle to manage and organize their data efficiently.
Additionally, non-compliance with data retention regulations can result in legal consequences and fines, especially in regions with strict data protection laws.
Furthermore, failing to delete or anonymize outdated customer data can hinder the business’s ability to maintain accurate records and can lead to confusion when interacting with customers.
However, businesses can overcome these challenges by opting for MyOperator call center tracking software, which complies with Data Retention and Deletion Policies.
MyOperator helps businesses establish clear and effective data retention policies that define how long customer data should be stored.
By adhering to these policies, MyOperator ensures that data is retained only for as long as necessary, reducing exposure to security risks and legal consequences.
6. Incident Response Plan
Without a structured plan, businesses face delayed response times to security incidents, leading to increased damage, potential regulatory consequences, operational disruption, customer dissatisfaction, and employee uncertainty during crises.
Which is why more than 10,000+ customers chose MyOperator as their call center software service as it stands out as a solution to these challenges, offering a well-defined Incident Response Plan as part of its comprehensive security measures.
MyOperator has a well-defined incident response plan in place. In the event of a data breach, this plan outlines immediate actions to contain the breach, notify affected parties, and minimize the impact.
7. Secure Data Centers
MyOperator’s virtual call center software is hosted in secure data centers that employ robust physical security measures, access controls, and redundancy to protect data from physical threats.
In conclusion, MyOperator’s commitment to data security is unwavering. With its ISO/IEC 27001:2013 compliance certification, MyOperator provides businesses with a secure environment for customer data.
Through robust encryption, strict access controls, compliance adherence, regular audits, and comprehensive employee training, MyOperator helps businesses maintain trust, comply with regulations, and thrive in a digital landscape where safeguarding customer data is of paramount importance.
Switch to a Secured Cloud Call Center Software Now.
Protect your data with the cloud solution.