Cloud platforms need to understand the regulatory parameters concerning cloud communication.
The growth of cloud Communication in the last decade has changed the way governments, businesses, and consumers store and process their data. India’s cloud computing scene is likely to grow rapidly with the adoption of AI (Artificial Intelligence), ML (Machine Learning), advanced analytics, and interactive media.
In short, cloud compliance is the process of abiding by the rules & regulations involving the use of cloud computing set by local, national, or international entities. The main pillars for ensuring compliance require certain elements like setting up of policies, compliance committee, staff training, timely reporting, monitoring & auditing, etc.

What is Regulatory Compliance?
Regulatory compliance refers to a set of rules which enterprises must follow to safeguard sensitive data and protect consumers against cybercrime. Businesses that deal with online/digital data, tools, processes, communications, etc. have to abide by these rules. Businesses that defy or fail to follow these rules can face severe penalties and ultimately lose a lot of money through hefty fines.
Essentially by strictly following compliance codes, a business can effectively get around troublesome data breaches. It ensures better data integrity and reliability. However, focusing only on data protection is not enough. Being able to respond promptly during a crisis is pivotal. The response needs to be quick, and effective in both physical and virtual domains.
For example, SOC 2 is a regulatory standard that dictates how companies should tackle customer data. A SOC 2 validation requires a company to focus strongly on security, processing integrity, availability, and privacy. The SOC 2 report for every company would be different, depending on its business practices. You can classify SOC 2 report into two categories – Type I and Type II. While the former is focuses on the company’s systems and its compliance with the trust frameworks, the latter is all about the overall efficiency of these systems in terms of operations.
Why do cloud communication platforms need to be compliant in 2023?
In 2022, cloud servers store more than 60% of all enterprise data. In 2015, this figure was only 30%. As more and more businesses use the cloud infrastructure to store petabytes of data – taking responsibility for keeping this data safe over time is important.
Failing to follow cloud communication compliance protocols can lead to financially debilitating data breaches. In 2022, the median cost of a data breach was more than $4 million as per IBM’s report. Effective cloud compliance helps businesses to capitalize on the innate benefits of cloud computing i.e. ease of data recovery, quick backup, high scalability, cost-efficiency, and more room for security upgrades.
Main advantages of ensuring proper compliance in cloud communication
Let us go over a few reasons that highlight the need for ensuring compliance as you grow your business:
More financial security
You probably will have to pay millions of dollars in fines if your company gets hit by a data breach. For example, non-compliance cost the banking sector more than $11 billion in 2020!
Prevent lawsuits
After experiencing a data breach due to compliance failure, your company will come under a lot of heat from judicial entities in the future. It will be susceptible to a never-ending flow of lawsuits.
Ensuring continuity & growth
Failure to maintain compliance standards can push your business towards bankruptcy through financial penalties, downtime, and loss of revenue.
Protection of brand image
Your brand is your biggest asset. Once you fall prey to a security breach after compliance failure – your brand image and reputation will take a huge hit. You can potentially lose millions in subscription revenue or sales revenue depending on the type of business you run.
Defense against cybercrime
Abiding by compliance protocol also ensures the safety of valuable business data from ransomware, malware, spam, insider misuse of sensitive data, etc.
How to migrate regulatory compliance with cloud communication?
A cloud migration process is highly complex and in-depth planning is vital for success. There are several factors to consider:
- Which applications do you move to the cloud along with the corresponding data?
- The process of moving applications and application data to the cloud.
- Selecting the migration strategy and the cloud structure depends on your company.
- The process of reducing security risks as much as possible.
- Selecting personnel who will work for the migration project, etc.
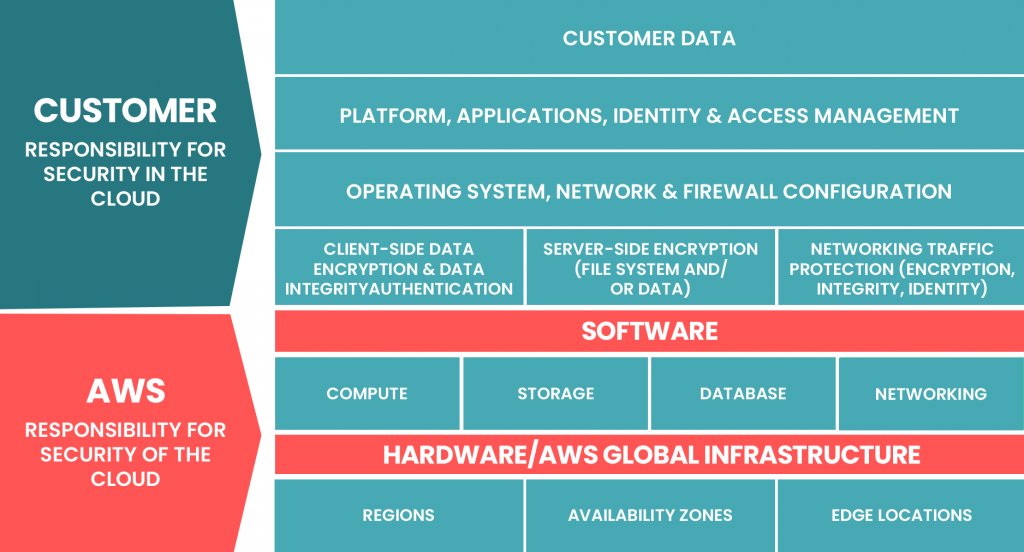
Regulatory compliance is a necessity for the cloud migration process, especially for sectors like finance and healthcare. You should be very thorough while evaluating which compliance rule applies to which dataset to prevent financial penalties. A Public Cloud environment is usually less secure as a lot of companies share their assets with other customers. This is why using a dedicated cloud environment is better. It offers more privacy and higher security from data leaks and breaches. It is important to ensure that the cloud infrastructure you’re using has international certifications for their data centers.
Important regulatory aspects you need to consider as a cloud telephony platform
Telecom service providers who are looking to migrate to the cloud need to understand the regulatory aspects of acquiring a license, Legal Interception (LI), and emergency services. This is how they can reduce costs, improve efficiency, and scale at a rapid pace. The General Data Protection Regulation (GDPR) and Digital Declaration are revolutionizing the compliance landscape throughout the world.
License acquisition
Getting a telecom license is anything but simple no matter which country you are talking about.
Legal Interception
It refers to accessing private communications between consumers or businesses legally e.g. text messages, emails, etc. for the sake of national security.
Emergency numbers
It is the responsibility of an enterprise to protect its employees by letting them make emergency calls using codes e.g. dialing (100) for police services in India.

Types of Compliance Programs Affecting Communication Security
Most communication systems under businesses are prone to data breaches. So, to prevent such issues we need to follow compliance programs. Let’s look at the ten compliance programs that are shaping communication security.
- Health Insurance Portability and Accountability Act (HIPAA)
- Health Information Technology for Economic and Clinical Health (HITECH)
- Payment Card Industry Data Security Standard (PC-IDSS)
- Service Organization Control (SOC)
- Sarbanes-Oxley Act
- International Organization for Standardization (ISO)
- General Data Protection Regulation (GDPR)
- Customer Proprietary Network Information (CPNI)
- Federal Information Security Management (FISM)
- Telephone Consumer Protection Act (TCPA)
Now, let’s compare SOC 2 & HIPAA to understand them better. While SOC 2 is a cloud-centric service that deals with sensitive data of consumers, HIPAA deals specifically with sensitive health data of patients. By having a robust SOC 2 coverage, your business would have a competitive advantage in the market. The incidences of security failures & risk exploitation would be lower, and the business will save a lot of money by not having to pay hefty fines to regulatory authorities. HIPAA benefits your healthcare business by providing a security protocol that enhances the safety culture between clients and patients and puts a stop to violations.
Conclusion
There are many challenges in migrating assets to the cloud for a telecom service under high-level regulation. However, in the long run, adopting a cloud call center solution has major advantages. To challenge your competitors you need to adopt new technologies. Using SaaS tools over a robust private cloud infrastructure can provide numerous benefits by acing every regulatory standard your business comes across.
Frequently Asked Questions (FAQs)
What are the 3 types of ISO?
The three types are – ISO 9001:2015, ISO 27001:2013, and ISO 14001:2015.
Why is ISO important?
ISO lays a strong foundation for national and international compliance for all businesses, including the ins and outs of the 27001 certification – helping them save a lot of time and increasing mobility expand internationally. The 27001 certification specifically focuses on information security management systems, ensuring organizations have the necessary measures in place to protect sensitive information and mitigate risks.
What is SOC 2 for dummies?
The Service Organization Control 2 is a security substructure that states how enterprises should govern, operate, and accumulate consumer data under the guidelines of Trust Services Categories (TSC).


